Article
Into the mobile maelstrom: What app-makers owe us
Banks, payment processors and merchants seek the loyalty of their customers; they owe their customers at least as much loyalty in the form of extra help to protect their money.

July 29, 2016
by Oren Kedem, Vice President of Product, BioCatch
Think your mobile device is safe enough to make payments with? A new cybercrime scam casts serious doubt on that safety. According to a report by security firm ProofPoint, even the most "secure" devices could be compromised by determined hackers carrying out the stunt, with the victim practically clueless about what is happening.
Many people — especially young people — practically "live" on their phones, as anyone who strolls down the street knows from the many faces buried in the contents of mobile device screens. The devices that allow them to communicate, express themselves, store information, and keep themselves entertained are constant companions.
And they're used for everything, including paying bills, making retail purchases and more. With apps such as PayPal, Venmo and Square now processing billions of dollars a month, credit cards and even cash are quickly going out of style.
 Hackers are quick to capitalize on any opportunity, and in recent months have developed a new scam that trades on device users' hunger for more content and entertainment.
Hackers are quick to capitalize on any opportunity, and in recent months have developed a new scam that trades on device users' hunger for more content and entertainment.
The DarkSideLoader scam involves loading devices with legitimate-looking but compromised clones of mobile apps. These clones contain malicious code can be used for all sorts of nefarious purposes.
The apps can be found on a number of sites that claim to offer "free" versions of games, business apps, utilities and entertainment content that device owners normally would have to pay for.
In order to gain access to these bootlegged apps, the device owner must first download an app loader signed with an enterprise app distribution certificate that makes anything it loads a trusted app.
These sites might seem like a great deal to anyone looking to save a few dollars — but there's a major downside. With hundreds of thousands of cracked apps on a site, there's a good chance that some of them will be infected with malware.
All a hacker has to do is send a rogue text message (for instance, "your mobile payment app needs to be updated") to a device with the app loader.
The unwitting user clicks on the message, triggering a download that replaces a legitimate version of PayPal or Venmo with a phony version that will swipe the individual's payment information and send it to Hacker Central (note that iPhones are just as vulnerable to this as Android devices).
Of course, this plan is one for ambitious, top-drawer hackers; it's really not necessary to work that hard to hijack a device or get at mobile app payment information.
For example, RATs, remote access tools that allow hackers to control a device, can easily be installed when the device user responds to a phishing message — delivered as an email, text, or socia media notification.
Via the message, a hacker can install a tool capable of gaining access to any app on the device, extracting data and sending it on to the hacker's servers. Or, hackers can simply use a banking or payment app to send themselves money or order items online and bill them to the victim.
One advantage for hackers on mobile devices is that most apps, including payment apps, will "trust" a device if told to do so. When apps are used on a trusted device, users don't have to reenter passwords or security codes — at most, they might be asked to press a confirmation button, which a hacker who controls the device with a RAT can easily do.
Given the extent of the problem, protection is a formidable task.
Of course, users need to take whatever steps they can to avoid problems. If your device has an aforementioned app loader, now might be the time to remove it, "free" cracked apps be damned.
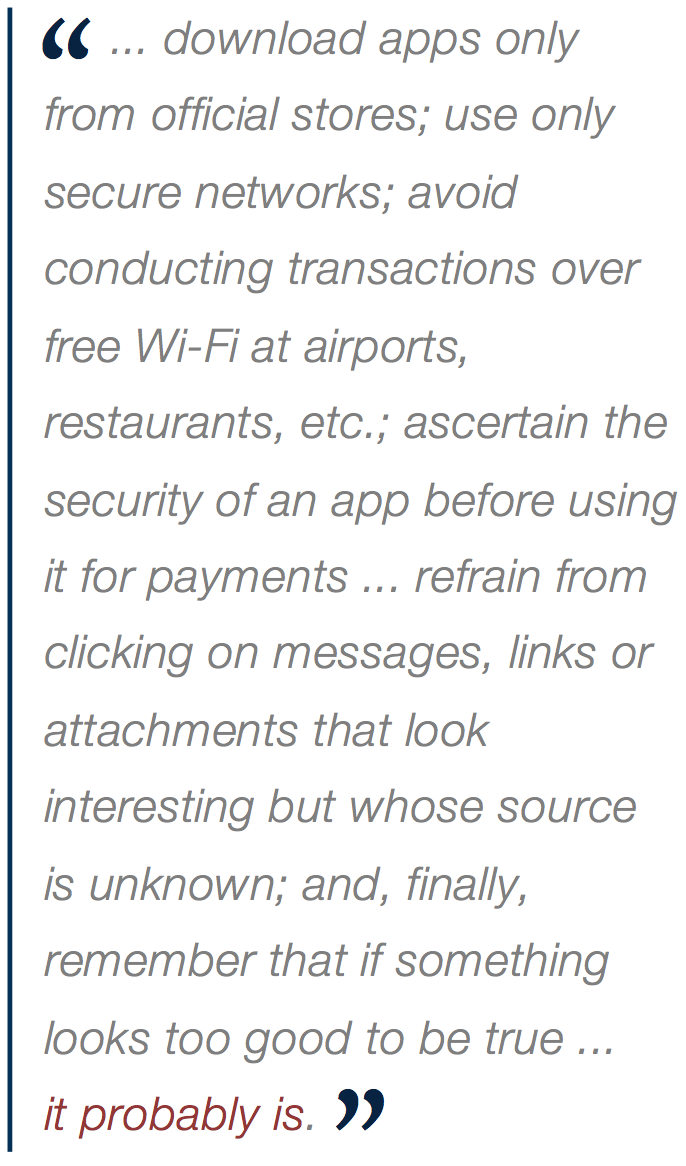
Further, device users should download apps only from official stores; use only secure networks; avoid conducting transactions over free Wi-Fi at airports, restaurants, etc.; ascertain the security of an app before using it for payments — or if the merchant has a history of breaches; refrain from clicking on messages, links, attachments, etc. that look interesting but whose source is unknown; and, finally, remember that if something looks too good to be true ... it probably is.
But beyond these local remediations that device owners can perform on their own, app-makers themselves need to get involved in security.
Behavioral biometrics — in which the identity of a user is verified based on surfing behavior — could go a long way to helping prevent fraud.
A service provider-side biometric measurement system that monitors and builds a profile based on how the customers holds a device, or touches, tabs, swipes and navigates through an app can help mobile apps detect an unauthorized user or bot trying to log in with legitimate credentials.
When the system detects a mismatch between a customer's activity and that customer's profile, it throws up a flag, barring further action until the situation is resolved.
The odds against mobile device users are just too formidable. Given the range of threats, it's extremely unlikely that they'll be able to avoid getting hit by hackers.
What's needed is a commitment by companies to connect mobile to new technologies that can help reduce attacks, if not eliminate them altogether.
Banks, payment processors and merchants seek the loyalty of their customers; they owe their customers at least as much loyalty, in the form of extra help to protect their money.
photo istock













