Security ResourcesPresented ByDiebold Nixdorf
Cybersecurity Threat Report 2025 by Diebold Nixdorf
In our annual threat reporting, we have remained committed to improvement in analyzing, communicating and tracking threat events targeting Diebold Nixdorf’s…
Presented by Diebold Nixdorf
download nowMindshare: The Case for ATM Outsourcing
Faced with constant change and security threats, DN customers shared why they decided to outsource the responsibility of managing their ATM fleets and why it…
Presented by Diebold Nixdorf
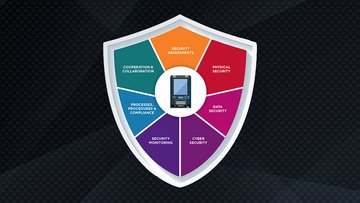
download nowSecurity Assessments with Diebold Nixdorf: Stay vigilant and up to date
Attack patterns and security technology change and develop quickly. To ensure your ATMs remain secure, Diebold Nixdorf suggests conducting regular security…
Presented by Diebold Nixdorf
download nowA Masterclass in ATM Security: Global Best Practices and Trends
In this webinar, security experts reflect on the current ATM attack landscape, its evolution and trends, and best practices in ATM security. Learn how to build…
Presented by Diebold Nixdorf
watch nowA Video Surveillance Guide for Financial Institutions
Banks and credit unions can replace fragmented, hardware-heavy surveillance with unified, cloud-ready platforms that support legacy cameras, reduce false…
Presented by Cook Solutions Group
download nowMalware in ATMs: Exploring Cyber Threats and Key Characteristics
ATM malware poses a persistent and evolving threat to financial institutions worldwide, exploiting vulnerabilities in critical devices to enable illicit…
Presented by Auriga
download nowTechnology-based Solutions for ATM and CIT Security
Intelligent security solutions are redefining what it means to protect cash. The convergence of physical and digital innovation is transforming ATM and CIT…
Presented by Secure Innovation
download nowATM Attack Explosive Testing (Live) – REPORT
'a2m active' and 'a2m passive' from Secure Innovation were put to the test with National Police in live ATM attack explosive testing with both solid and gas…
Presented by Secure Innovation
download now12 Strategies to Prevent ATM Fraud - An ATM Terminal Security Guide
Strengthen your ATM security with our expert insights! Get the complete Multi-Layered Security Defense Strategy by downloading our ATM Terminal Security…
Presented by Cook Solutions Group
download nowVendor Risk Management Guide For Financial Institutions
Discover how vendor consolidation can elevate security, efficiency, integration opportunities, and cost savings!
Presented by Cook Solutions Group
download nowATM SECURITY LANDSCAPE AND FORECAST: AN IN-DEPTH ANALYSIS
Auriga offers an in-depth analysis of the most frequent attacks on ATMs, including a history of the most dangerous malware attacks.
Presented by Auriga
download nowDefending Against Jackpotting Threats: A Comprehensive Guide
As the digital landscape continues to evolve, so do the methods employed by criminals seeking illicit gains. In 2018, the U.S. Secret Service sounded the alarm…
Presented by Cook Solutions Group
download nowUnveiling the Threat of Deep Insert Skimming: Safeguarding Against ATM Fraud
This whitepaper delves into the emerging threat of deep insert skimming, a sophisticated form of ATM fraud characterized by wafer-thin devices hidden inside…
Presented by Cook Solutions Group
download nowSecuring Financial Systems: Mitigating Man-in-the-Middle (MITM) Attacks
This article explores the threat landscape of Man-in-the-Middle (MITM) attacks on ATMs and ITMs, shedding light on the methods and goals of attackers. By…
Presented by Cook Solutions Group
download nowRight to Repair
The Right to Repair means you're actually in the driver's seat when it comes to selecting & partnering with an independent service provider or even choosing to…
Presented by Burroughs, Inc.
download nowDigital Transformation Technologies To Implement For 2023
When you’re responsible for ensuring your organization’s day-to-day operations run smoothly, securely, and reliably, it can be difficult to find time to look…
Presented by Burroughs, Inc.
download nowBanks can fight back against ATM Jackpotting
Recently, a new ATM jackpotting malware variant, dubbed FiXS, has been identified as a new threat infecting ATMs to steal large amounts of cash. What exactly…
Presented by Auriga
download now2021 ATM and Self-service Software Trends and Analysis
For the 14th consecutive year, ATM Marketplace and KAL ATM Software have partnered to publish the ATM industry's most influential and insightful annual guide…
Presented by KAL ATM Software GmbH
watch nowNew standard set to revolutionize the ATM world
The ATM industry is now at the beginning of creating the new standard that will eventually take over and provide enormous benefits to all ATM stakeholders…
Presented by KAL ATM Software GmbH
watch nowWhat Can a Cash Recycler Do For Your Organization
Cash recyclers are able to accept, dispense, and secure cash that comes in and out of your business via daily transactions, there’s much more to them than that.
Presented by Burroughs, Inc.
download now